Confidential Containers pattern

Validation status:
Links:
About the Confidential Containers pattern
Confidential computing is a technology for securing data in use. It uses a Trusted Execution Environment provided within the hardware of the processor to prevent access from others who have access to the system. Confidential containers is a project to standardize the consumption of confidential computing by making the security boundary for confidential computing to be a Kubernetes pod. Kata containers is used to establish the boundary via a shim VM.
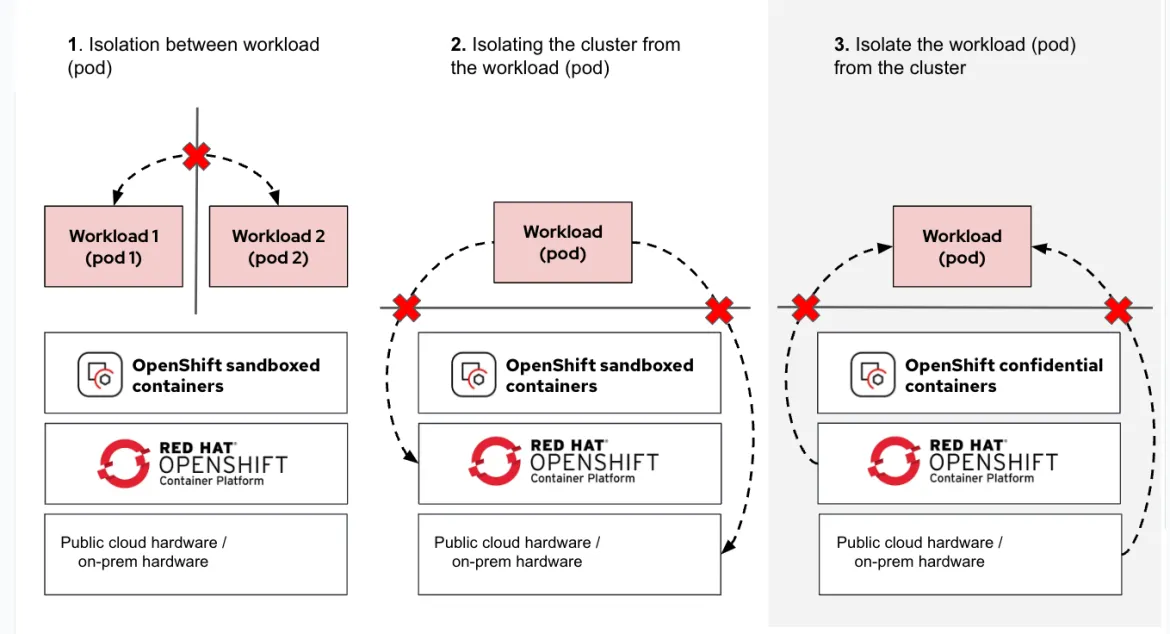
A core goal of confidential computing is to use this technology to isolate the workload from both Kubernetes and hypervisor administrators.

This pattern uses Red Hat OpenShift sandbox containers to deploy and configure confidential containers on Microsoft Azure.
It deploys three copies of 'Hello OpenShift' to demonstrate some of the security boundaries that enforced with confidential containers.
Requirements
An an azure account with the required access rights
An OpenShift cluster, within the Azure environment updated beyond 4.16.10
Security considerations
This pattern is a demonstration only and contains configuration that is not best practice
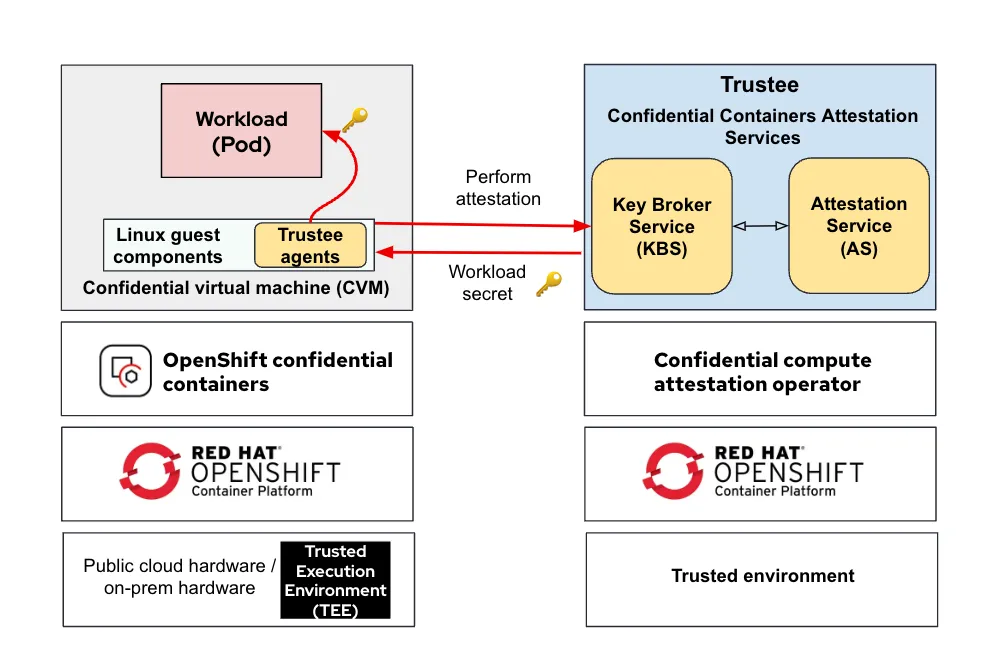
The default configuration deploys everything in a single cluster for testing purposes. The RATS architecture mandates that the Key Broker Service (e.g. Trustee) is in a trusted security zone.
The Attestation Service has wide open security policies.
Future work
Deploying the environment the 'Trusted' environment including the KBS on a separate cluster to the secured workloads
Deploying to alternative environments supporting confidential computing including bare metal x86 clusters; IBM Cloud; IBM Z
Finishing the sample AI application
Architecture
Confidential Containers typically has two environments. A trusted zone, and an untrusted zone. In these zones, Trustee, and the sandbox container operator are deployed, respectively.
For demonstration purposes the pattern currently is converged on one cluster**