git clone git@github.com:your-username/amx-accelerated-multicloud-gitops.gitDeploying the Intel AMX accelerated Multicloud GitOps pattern
An OpenShift cluster
To create an OpenShift cluster, go to the Red Hat Hybrid Cloud console and select Services -> Containers -> Create cluster.
The cluster must have a dynamic
StorageClassto provisionPersistentVolumes.Cluster sizing requirements.
Optional: A second OpenShift cluster for multicloud demonstration.
The use of this pattern depends on having at least one running Red Hat OpenShift cluster. However, consider creating a cluster for deploying the GitOps management hub assets and a separate cluster for the managed cluster.
If you do not have a running Red Hat OpenShift cluster, you can start one on a public or private cloud by using Red Hat Hybrid Cloud Console.
Fork the multicloud-gitops-amx repository on GitHub.
Clone the forked copy of this repository.
Create a local copy of the secret values file that can safely include credentials for the config-demo application and edit it if you want to customize the secret. If not, the framework generates a random password.
cp values-secret.yaml.template ~/values-secret-multicloud-gitops.yamlDo not commit this file. You do not want to push personal credentials to GitHub.
(Optional) You may customize the deployment for your cluster depending on your needs by editing values-global.yaml and values-hub.yaml. To do this run the following commands:
git checkout -b my-branchvi values-global.yamlgit add values-global.yamlgit commit values-global.yamlgit push origin my-branchDeploy the pattern by running
./pattern.sh make installor by using the Validated Patterns Operator - both methods are described below.
Deploying the cluster by using the pattern.sh file
To deploy the cluster by using the pattern.sh file, complete the following steps:
Login to your cluster by running the following command:
oc loginOptional: Set the
KUBECONFIGvariable for thekubeconfigfile path:export KUBECONFIG=~/<path_to_kubeconfig>Deploy the pattern to your cluster. Run the following command:
./pattern.sh make install
Verify that the Operators have been installed.
To verify, in the OpenShift Container Platform web console, navigate to Operators → Installed Operators page.
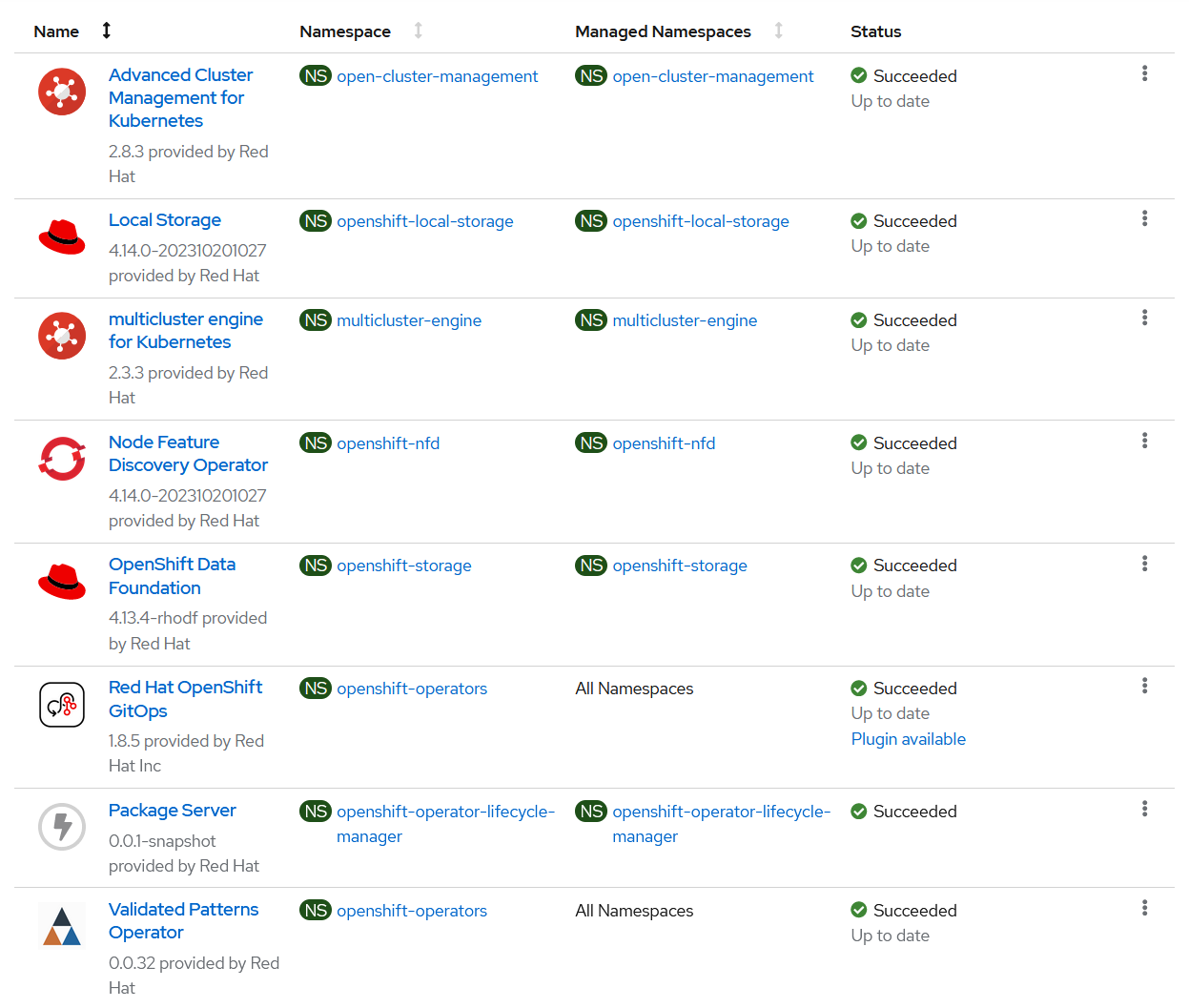
Check that the following Operators are installed with
Succeededstatus (Figure 1):Advanced Cluster Management for Kubernetes
multicluster engine for Kubernetes
Node Feature Discovery Operator
Red Hat Openshift GitOps
Validated Patterns Operator
Deploying the cluster by using the Validated Patterns Operator
To install the Validated Patterns Operator:
Log in to the Openshift Container Platform web console and select Operators > OperatorHub.
Search for Validated Patterns Operator, open it and click Install.
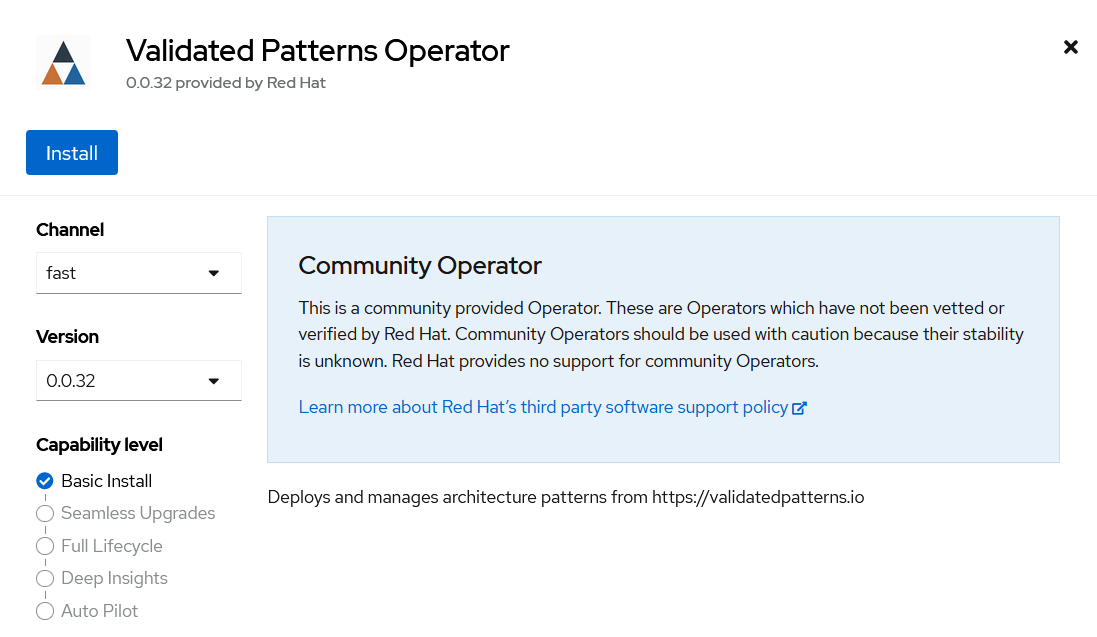 Figure 2. Install Validated Patterns Operator
Figure 2. Install Validated Patterns OperatorChoose default settings for the installation mode, namespaces and update strategy and confirm it by clicking Install.
Select Operators > Installed Operators.
Ensure that Validated Patterns Operator is listed in the
openshift-operatorsproject with a statusSucceeded.
After succeeded installation open Validated Patterns Operator, go to Pattern tab and click Create Pattern.
Fill the Name of the pattern
multicloud-gitops-amxand Cluster Group Namehub(from values-global.yaml file).Under Git Config > Target Repo copy the link to your fork and under Git Config > Target Revision write the name of your branch (Figure 3).
Click Create to create the pattern.
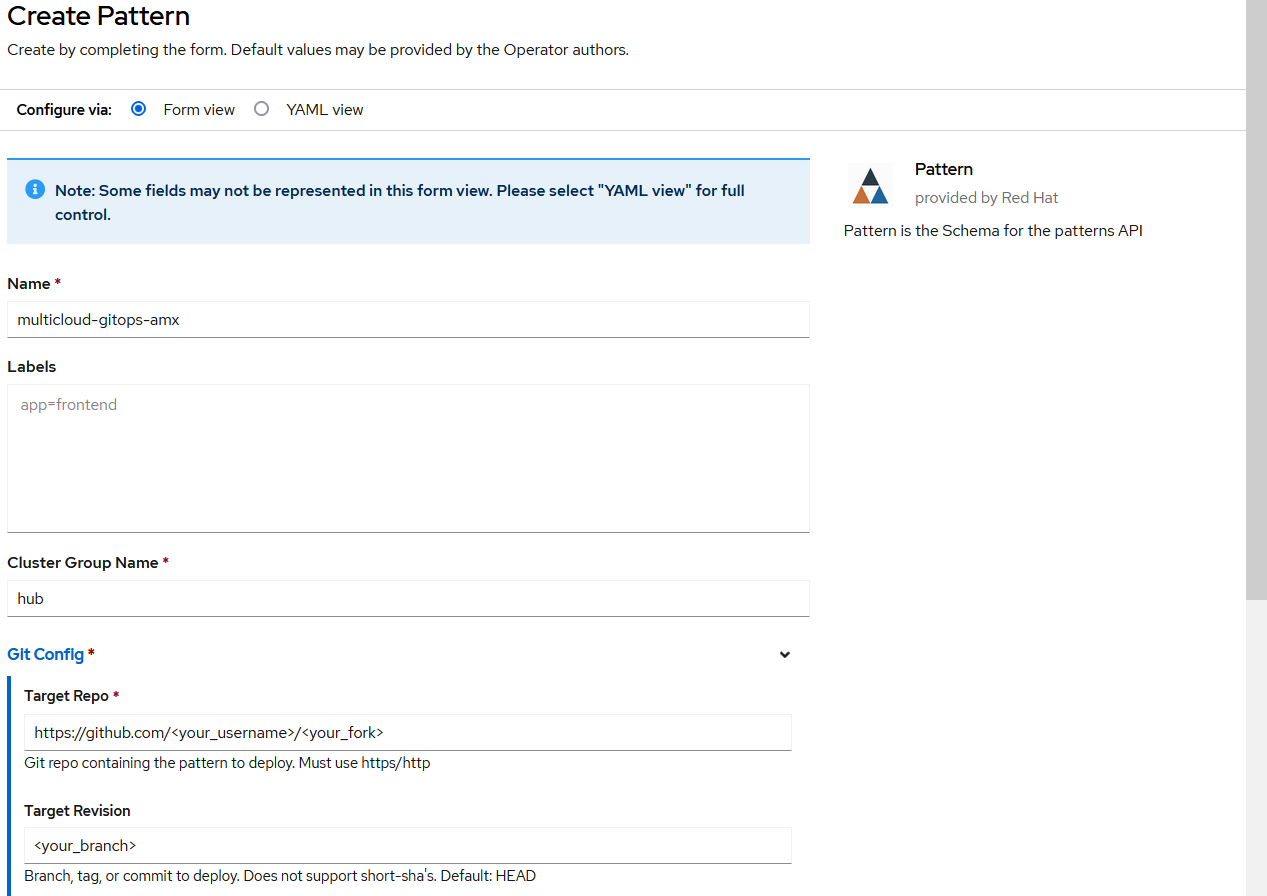 Figure 3. Create Pattern Form
Figure 3. Create Pattern Form
Verify that the rest of Operators have been installed:
To verify, in the OpenShift Container Platform web console, navigate to Operators → Installed Operators page.
Check that the following Operators are installed with
Succeededstatus (Figure 1):Advanced Cluster Management for Kubernetes
multicluster engine for Kubernetes
Node Feature Discovery Operator
Red Hat Openshift GitOps
Add a secret for config-demo application (from values-secret-multicloud-gitops.yaml) to Vault manually:
Go to Vault service route. URL can be found:
by running command:
oc -n vault get route vault -ojsonpath='{.spec.host}'in Openshift Container Platform web console under Networking > Routes for
vaultproject.
Log into the Vault using root token. Root token can be found by executing command:
oc -n imperative get secrets vaultkeys -ojsonpath='{.data.vault_data_json}' | base64 -dAfter login go to
secretcatalog and clik Create secret and fill all the fields manually (Figure 2):Path for this secret is
global/config-demo(from values.yaml file forconfig-democharts)Under Secret data key is
secret(from values-secret-multicloud-gitops.yaml file) and in next field put its value.Click Add and then Save.
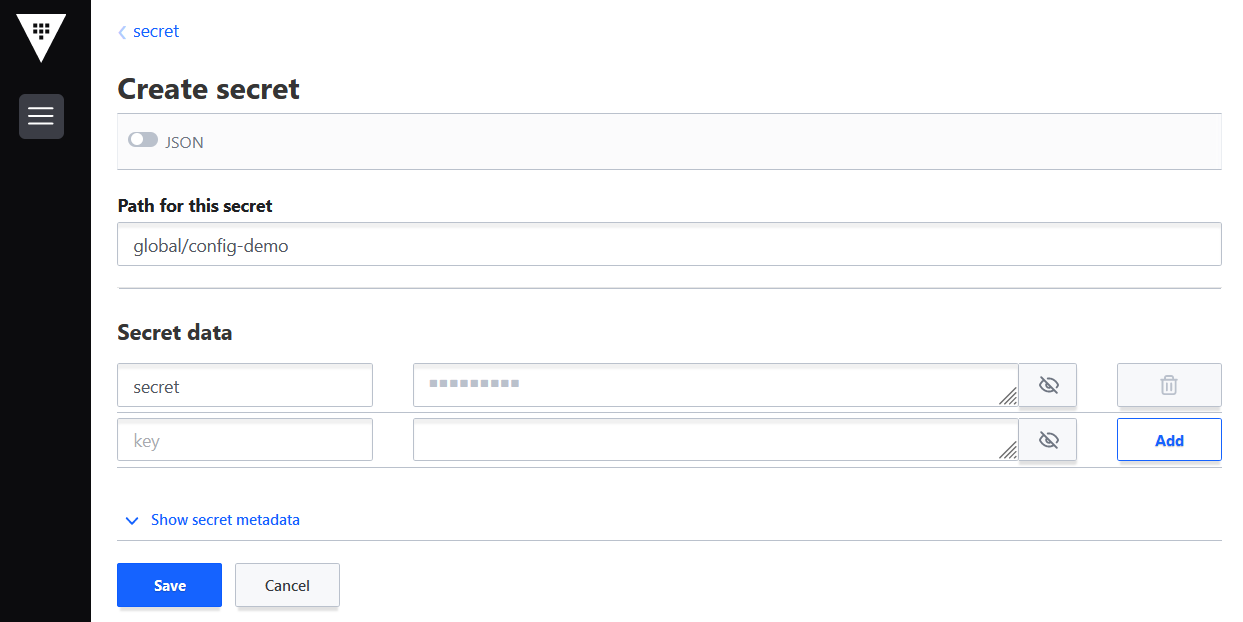 Figure 4. Create secret
Figure 4. Create secret
Verification
Go to the Hub ArgoCD and verify that all applications are synchronized. The URL can be found in Openshift Container Platform web console under Networking > Routes for the project multicloud-gitops-amx-hub or use command:
oc -n multicloud-gitops-amx-hub get route hub-gitops-server -ojsonpath='{.spec.host}'All applications should be Healthy and Synced:
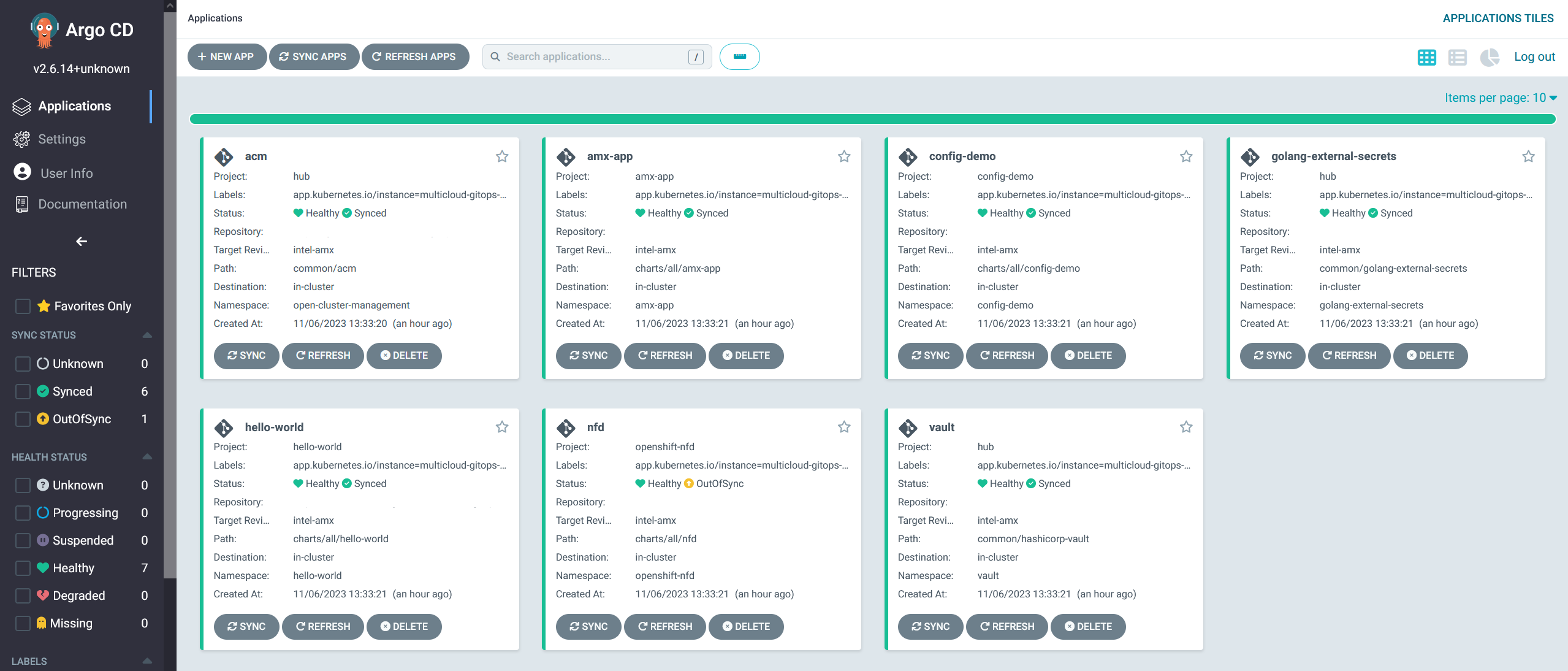
amx-appCheck the logs of a pod amx-app to verify if it uses Intel AMX. In the OpenShift Container Platform web console, navigate to Workloads > Pods. Change project to amx-app and open the Logs tab in the pod details. The appearance of avx_512_core_amx_bf16 flag on the list of compiled instructions confirms that Intel AMX is used.
As part of this pattern, HashiCorp Vault has been installed. Refer to the section on Vault.
Next steps
After the management hub is set up and works correctly, attach one or more managed clusters to the architecture.
For instructions on deploying the edge, refer to Attach a managed cluster (edge) to the management hub.